rc4解密函数分析
首先初始化了一些变量
var _0x31b35b = [],
_0x2d6c29 = 0x0,
_0x24b4f5,
_0x196a93 = "",
_0x56258a = "";
然后调用原生的atob,传入我们数组混淆里的字符得到一个乱序字符
_0x11262d = atob(_0x11262d);
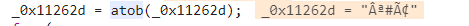
遍历索引,获取UTF-16字符,然后调用toString到十六进制,然后拼上00,取后两位,再加%
for (
var _0x3d7663 = 0x0, _0x34f9e9 = _0x11262d["length"];
_0x3d7663 < _0x34f9e9;
_0x3d7663++
) {
_0x56258a +=
"%" +
("00" + _0x11262d["charCodeAt"](_0x3d7663)["toString"](0x10))[
"slice"
](-0x2);
}
对所有进行循环处理后
调用decodeURIComponent进行解码
_0x11262d = decodeURIComponent(_0x56258a);
还是一个乱序的
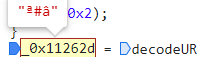
然后声明了一个256字符的对应数组
for (var _0x48101c = 0x0; _0x48101c < 0x100; _0x48101c++) {
_0x31b35b[_0x48101c] = _0x48101c;
}
然后又进入了一个小循环,循环256次
_0x2d6c29 初始化为0
_0x2d6c29 =_0x2d6c29 +循环次数+传入的第二个参数按顺序取字符"SRfb"循环code值
再%256一下
然后将计算出来的位置与当前位置做一次互换,这里说实话意义不是特别懂...
for (_0x48101c = 0x0; _0x48101c < 0x100; _0x48101c++) {
_0x2d6c29 =
(_0x2d6c29 +
_0x31b35b[_0x48101c] +
_0x148d0f["charCodeAt"](_0x48101c % _0x148d0f["length"])) %
0x100;
_0x24b4f5 = _0x31b35b[_0x48101c];
_0x31b35b[_0x48101c] = _0x31b35b[_0x2d6c29];
_0x31b35b[_0x2d6c29] = _0x24b4f5;
}
_0x48101c = 0x0;
_0x2d6c29 = 0x0;
然后开始循环字符
_0x48101c 每次加一,满256循环一次
_0x2d6c29取_0x2d6c29与上面的字母表映射累加取余256
然后取表又做了一次互换...
然后计算出来字符...说实话不太懂含义
for (var _0x206f10 = 0x0; _0x206f10 < _0x11262d["length"]; _0x206f10++) {
_0x48101c = (_0x48101c + 0x1) % 0x100;
_0x2d6c29 = (_0x2d6c29 + _0x31b35b[_0x48101c]) % 0x100;
_0x24b4f5 = _0x31b35b[_0x48101c];
_0x31b35b[_0x48101c] = _0x31b35b[_0x2d6c29];
_0x31b35b[_0x2d6c29] = _0x24b4f5;
_0x196a93 += String["fromCharCode"](
_0x11262d["charCodeAt"](_0x206f10) ^
_0x31b35b[(_0x31b35b[_0x48101c] + _0x31b35b[_0x2d6c29]) % 0x100]
);
}
最后得出ert
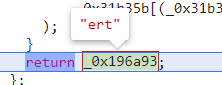
并将其存入表中
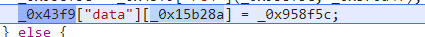
大概理解了我们可以直接整理下js字符串了
直接替换下加密函数,然后删除数组啥的,再删除表示运行看看

可以看到会弹窗
let a = 0x1;
alert(a);
(function (_0xc2361a, _0x49f6b2, _0x4c5d49) {
var _0x4bbdd6 = {
PTyWI: 'ert',
CFOau: function _0x2e9886(_0x27d2c4, _0x233ed3) {
return _0x27d2c4 !== _0x233ed3;
},
yGZoO: 'undefined',
UQhqT: function _0xe650a3(_0x4590a1, _0x160226) {
return _0x4590a1 === _0x160226;
},
TtTMq: 'jsjiami.com.v5',
FQggo: function _0x47c22c(_0x2fe61e, _0x50381a) {
return _0x2fe61e + _0x50381a;
},
FTCAn: '删除版本号,js会定期弹窗',
};
_0x4c5d49 = "al";
try {
_0x4c5d49 += _0x4bbdd6["PTyWI"];
_0x49f6b2 = encode_version;
if (
!(
_0x4bbdd6["CFOau"](
typeof _0x49f6b2,
_0x4bbdd6['yGZoO']
) &&
_0x4bbdd6['UQhqT'](
_0x49f6b2,
_0x4bbdd6['TtTMq']
)
)
) {
_0xc2361a[_0x4c5d49](_0x4bbdd6["FQggo"]("删除", '版本号,js会定期弹窗,还请支持我们的工作'));
}
} catch (_0x2d647c) {
_0xc2361a[_0x4c5d49](_0x4bbdd6['FTCAn']);
}
})(window);
encode_version = "jsjiami.com.v5";
主要看判断部分
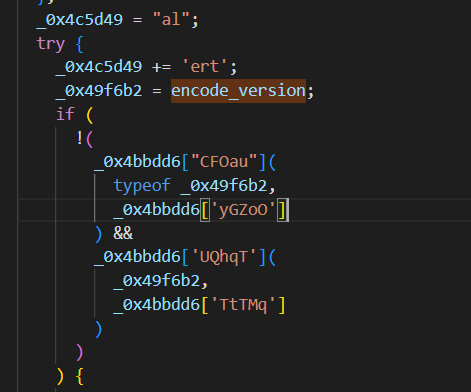
走了这几个函数,这些都是一些花指令,叫做【花指令混淆】
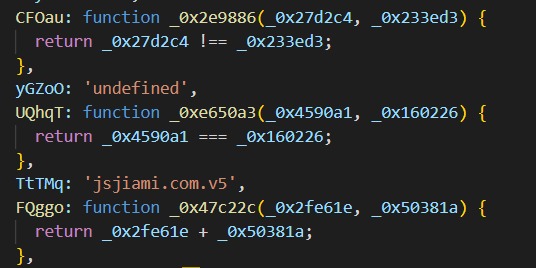
下面判断字符串是否为undefined,并且该函数是否等于TtTMq,如果任意一个为假则提示弹窗
如果删除encode_version会触发catch也会触发弹窗,我们直接设置为true然后删除就行
就破除版权了
try {
_0x4c5d49 += 'ert';
_0x49f6b2 = encode_version;
if (
!(//判断字符串是否为undefined,并且该函数是否等于TtTMq,如果任意一个为假则提示弹窗
_0x4bbdd6["CFOau"](
typeof _0x49f6b2,
_0x4bbdd6['yGZoO']
) &&
_0x4bbdd6['UQhqT'](
_0x49f6b2,
_0x4bbdd6['TtTMq']
)
)
) {
_0xc2361a[_0x4c5d49](_0x4bbdd6["FQggo"]("删除", '版本号,js会定期弹窗,还请支持我们的工作'));
}
} catch (_0x2d647c) {
_0xc2361a[_0x4c5d49](_0x4bbdd6['FTCAn']);
}
结语
于是你看了一大堆除了学到一堆混淆名字以及如何破最简单的加密的版权....

